Cyber Security
ThunderCat enables customers to leverage real-time analytics to bring focus to their current security architectures. This helps customers break the cycle of detection and remediation and more efficiently protect enterprise assets.
Cyber Security
Defensive Cyber operations is a challenging and constantly evolving space. The threat landscape of today is polymorphic, with shifting variables and risk. Many customers are forced to be reactionary in making decisions about their security architecture. These reactions are driven by government mandate and regulation, new projects, or emerging threats.
ThunderCat works with our customers to break this reactionary cycle and help make strategic architectural decisions. By approaching the problem in a focused and pragmatic way. ThunderCat enables customers to Assess, Plan, and Implement within a strategic and durable process. Helping customer do more with less, reduce operational cost, and gain value from their Cyber product acquisitions.
We are focused on selling best of breed and innovative products in the Cyber and Analytics space. ThunderCat offers Cyber solutions across several different solutions areas:
Government Mandate & Regulation
- Helping customers in responding to larger government mandate EO14028 & associated Memoranda (M21-31, M22-01, M22-09)
- Strategic Planning and Advisory Services around CMMC
- Regulatory Compliance (GDPR, PCI, HIPPA, etc…)
Cyber Analytics
- Building an Enterprise Security Dataplane. Allowing organizations to collect the right data once. Move the right data to the right place, at the right time. Delivering more signal to customer SIEM, Data Lake, Cold Storage, and less noise.
- There has been an explosive growth of data sources, coupled with the challenges of collecting, prepping, storing, and analyzing data. ThunderCat specializes in engineering innovative and cost effective security data lake architecture.
SecOps Automation
ThunderCat helps customers move from traditional operations to a CI/CD focused security operations .
- This includes engineering SOAR (Security Orchestration, Automation, and Response) solutions to lessen the operational burden.
- Deploying automated Hunt capabilities, leveraging Detections as Code and modern SecOps principles
- Architecting faster Incident Response solutions, using playbook-driven automation
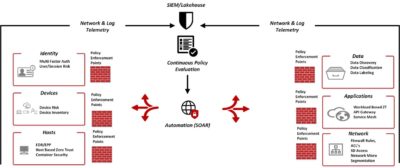
Zero Trust
- ThunderCat assists customers in assessing their current ZT capabilities, gaps, and toolsets to fill those gaps.
- Instead of recommending point solutions, ThunderCat leverages our experienced engineering team to help customers choose the right solutions that meet multiple security objectives.
- ThunderCat understands that Zero Trust is a culture (not a product, tool, or singular process). We proactively help our customer blend this culture into their existing defensive cyber architectures.
For more information on our cyber solutions, please contact us.
